Information Security and Privacy Protection
Information security is critical to ensuring business stability and maintaining stakeholder trust. Acer Gadget places high importance on cybersecurity, fully aligning with Acer Group’s policies and standards, with a long-term goal of strengthening security management. Through organizational mechanisms, standardized processes, and regular drills, the Company has built a forward-looking and resilient information security framework to safeguard digital assets and data security.
Information Security
Acer Gadget implements information security in line with Acer Group’s Information Security Policy and
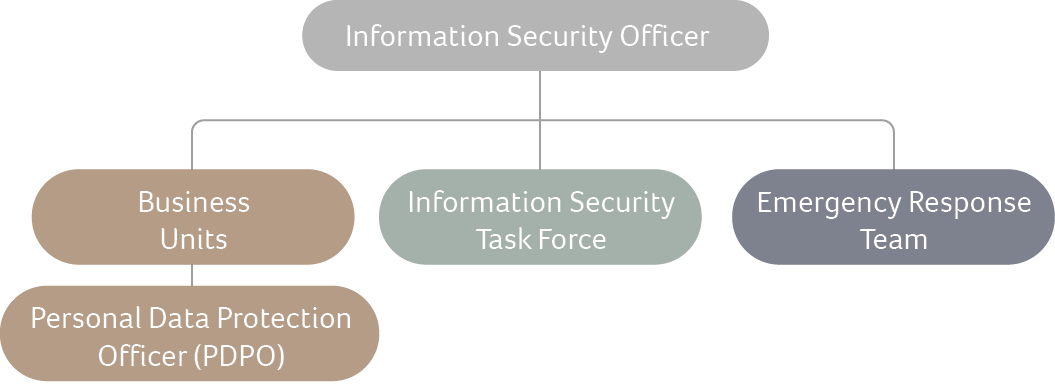
coordinates with the Group’s global information security management organization. A designated Information Security Officer leads IT staff to integrate business and R&D resources, ensuring the effectiveness of security mechanisms. Regular risk assessments and audits with Acer headquarters strengthen compliance and response capabilities. Although ISO 27001 certification has not yet been obtained, all practices follow Acer Group standards, and an incident response plan is in place for immediate activation in case of cybersecurity incidents, including:



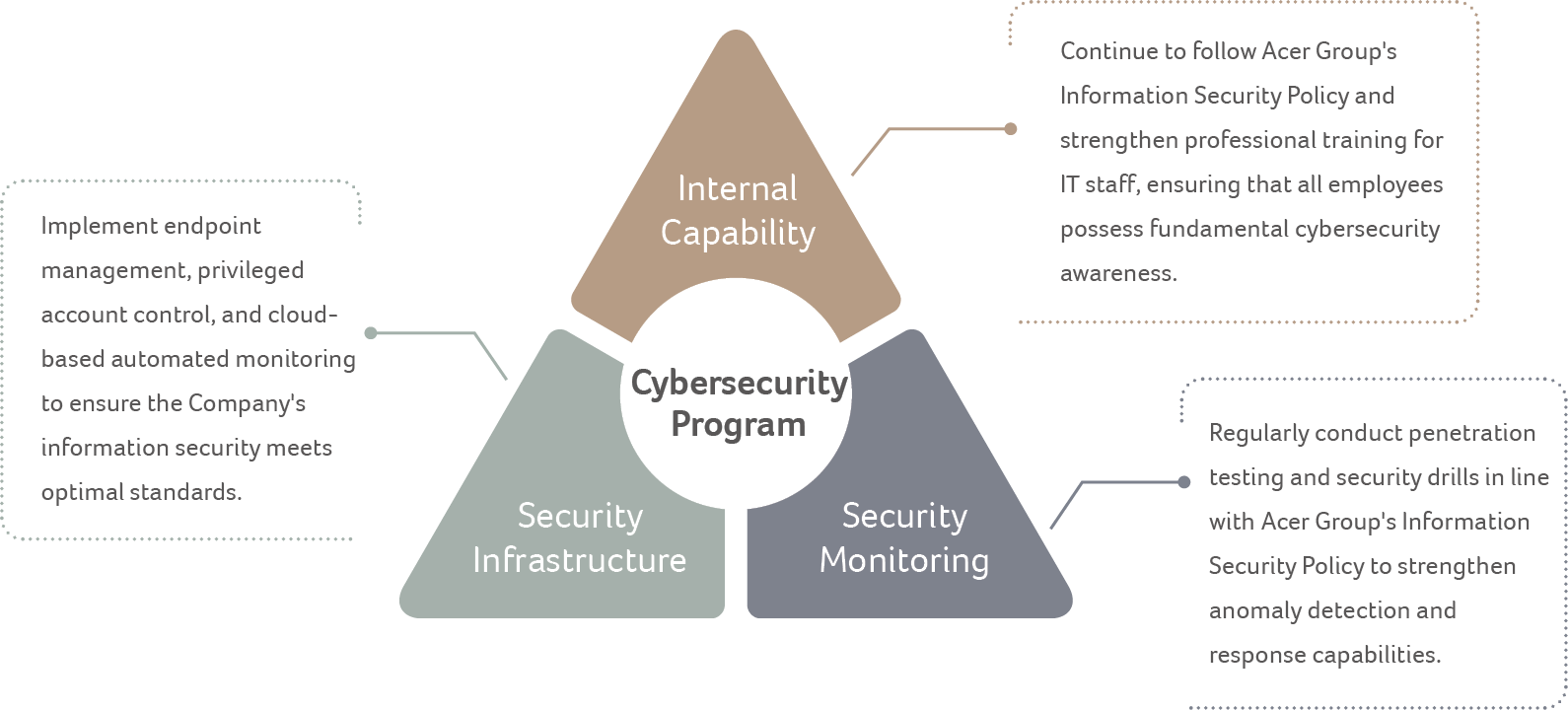
To strengthen information security resilience, Acer Gadget has also launched a long-term cybersecurity enhancement program, focusing on:
Acer Gadget Information Security Protection Organization
Information Security Strategy
To ensure information security, Acer Gadget has fully adopted Acer Group’s information security management framework. A designated Information Security Officer leads the IT team in implementing security enhancement measures to ensure the continuous optimization and enforcement of security mechanisms. Through regular internal risk assessments and close collaboration with Acer headquarters’ security team, Acer Gadget ensures that its information security strategy meets business needs and regulatory requirements. The core strategies are as follows:
Strengthening Information Security Policies and Framework
Network Security and Access Control
Account and Access Rights Management
Endpoint Security and Application Protection
Incident Response and Recovery Capability
Backup and Disaster Recovery Mechanisms
Long-term Security Program
Information Security Training and Awareness
To strengthen employees’ awareness of information security, Acer Gadget continues to promote education and training in line with Acer Group’s Information Security Policy. The 2024 training achievements are as follows:
● Information Security Online Training: In 2024, a total of 97 participants completed online training courses covering topics such as the Information Security Policy, security processes, social engineering prevention, and common attack techniques.
● Privacy Protection Training: In 2024, a total of 41 participants attended Acer’s global privacy protection training, which included principles of personal data protection, data handling standards, and risk identification and management.
In addition, Acer Gadget continues to strengthen its security defense capabilities through courses and practical exercises, enhancing employees’ protective and response skills. This builds a robust governance mechanism to address the growing challenges of cybersecurity threats.
Privacy Protection
Acer Gadget complies with Acer Group’s global privacy protection framework, including the Acer Group Personal Data Protection Management Policy and Personal Information Management Principles, and is committed to safeguarding the personal data of customers, employees, and partners. All data collection, processing, and storage activities are conducted in accordance with applicable regulations and internal policies. To ensure privacy and information security, the Company has appointed a Personal Data Custodian responsible for implementing relevant policies, and works closely with Acer Group’s information security and legal departments to ensure the effective enforcement of personal data protection mechanisms.
● Compliance with International Standards: Acer Gadget follows ISO 27701 (Personal Information Management System), the EU GDPR (General Data Protection Regulation), and Taiwan’s Personal Data Protection Act to ensure privacy protection meets both international and local requirements.
● Privacy Management Mechanisms: The Company has established internal privacy protection guidelines requiring all units involved in personal data processing—covering customer data, employee information, and supply chain partner data—to comply with the Personal Information Management Principles and related internal rules.
● Transparent Data Processing: Acer Gadget ensures that all personal data collection, use, and storage are conducted legally and ethically, with clear notification to data subjects regarding their rights and the scope of use.
● In 2024, 41 participants completed Acer’s global privacy protection training, covering privacy principles, personal data processing, and risk management.
● Regular internal privacy training is also conducted to ensure all employees maintain privacy awareness and risk prevention capabilities.
● Privacy Risk Assessment: Conduct regular internal privacy risk assessments with Acer’s security team to identify potential risks and improve protection mechanisms.
● Access Rights Management: Apply the principle of least privilege to ensure only authorized personnel can access specific personal data.
● Data De-identification Technologies: Encrypt and de-identify sensitive data to minimize the risk of data leakage.
● Personal Data Incident Response: In the event of a data breach, the Company will activate its information security and privacy response plan, promptly notify Acer Group’s security and legal teams, and conduct incident investigation and remediation.
● Stakeholder Grievance Mechanism: A comprehensive personal data management and complaint-handling mechanism is in place to ensure that customers and employees can raise privacy concerns through stablished grievance channels.
